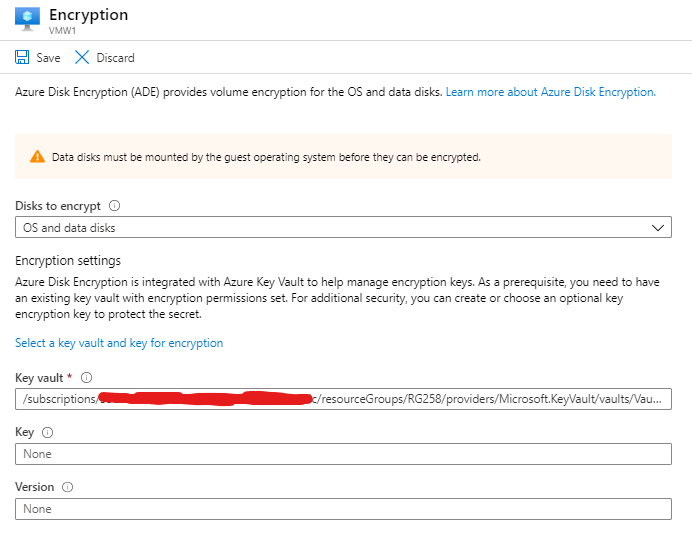
Enable Azure Disk Encryption
2020年02月23日
PS ###> cd $HOME\clouddrive
PS ###/clouddrive> vim create_vm.ps1
Executing this PS script will launch the VM, together with relevant resources such as resource group.
PS ###/clouddrive> ./create_vm.ps1
PS ###/clouddrive> New-AzKeyvault -name "Vault258new" -ResourceGroupName "RG258" -Location "westus" -EnabledForDiskEncryption
PS ###/clouddrive> Set-AzKeyVaultAccessPolicy -VaultName "Vault258new" -ResourceGroupName "RG258" -EnabledForDiskEncryption
PS ###/clouddrive> Get-AzureRmVmDiskEncryptionStatus -ResourceGroupName "RG258" -VMName "VM1" tionKeyVaultId $KeyVaultResourceId -VolumeType "All"
PS
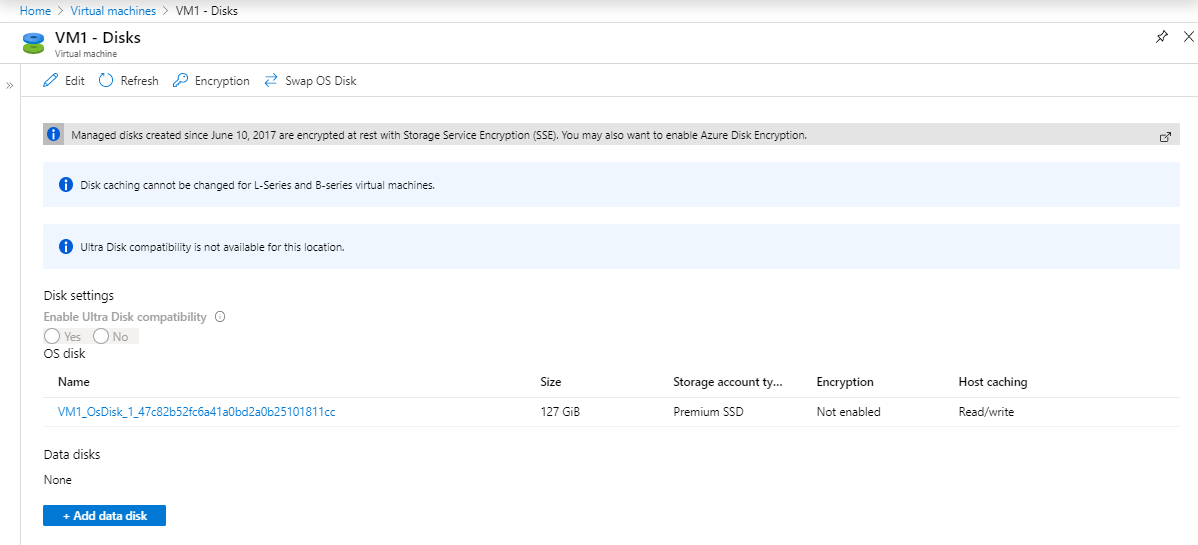
Show the status from the Azure portal.
Enable Azure Disk Encryption on volumes that are of all types. Execute the PowerShell script in CloudShell.
PS ###/clouddrive> vim ./create_vm1_ade.ps1
PS ###/clouddrive> ./create_vm1_ade.ps1
After execute below command, check the encryption status of the OS disk.
(On July 20, 2020:)
>> -Location "WestUS" `
>> -CreateOption Empty `
>> -DiskSizeGB 32
>> -ResourceGroupName "RG258" `
>> -DiskName "VM1-Disk3" `
>> -Disk $diskConfig
PS ###/clouddrive> $vm = Get-AzVM -ResourceGroupName "RG258" -Name "VM1"
PS ###/clouddrive> vim ./create_vm1_datadisk.ps1
Initialize Disk and create Partition, by executing below comamnd:
PS C:\Users\scadmin> manage-bde -status F:
Go to Azure CloudShell. Execute below command:
PS ###/clouddrive> vim create_vm1_ade_new_disk.ps1
PS ###/clouddrive> ./create_vm1_ade_new_disk.ps1
PS C:\Users\scadmin> manage-bde -status F:
PS ###/clouddrive> Get-AzureRmVmDiskEncryptionStatus -ResourceGroupName "RG258" -VMName "VM1"
References
Using the Resource Manager template
Get-AzureRmVMDiskEncryptionStatus
manage-bde -status c:
https://helpdesk.eoas.ubc.ca/kb/articles/how-to-check-status-of-bitlocker-encryption-on-a-client-on-windows-10
https://github.com/Azure/azure-quickstart-templates/tree/master/201-encrypt-running-windows-vm-without-aad
Pre-requisites
Create VM.PS ###> cd $HOME\clouddrive
PS ###/clouddrive> vim create_vm.ps1
$ResourceGroupName = "RG258" $LocationName = "westus" $VNetName = "RG258-vnet" $ImageName = "Win2016Datacenter" $SubnetName = "default" $SecurityGroupName = "VM1nsg828" $VMSize = "Standard_B2ms" $VMName = "VM1" New-AzVm ` -ResourceGroupName $ResourceGroupName ` -Location $LocationName ` -Image $ImageName ` -VirtualNetworkName $VNetName ` -SubnetName $SubnetName ` -SecurityGroupName $SecurityGroupName ` -Size $VMSize ` -Name $VMName
Executing this PS script will launch the VM, together with relevant resources such as resource group.
PS ###/clouddrive> ./create_vm.ps1
cmdlet New-AzVM at command pipeline position 1
Supply values for the following parameters:
Credential
User: scadmin
Password for user scadmin: ************
ResourceGroupName : RG258
Id : /subscriptions/35c3c9dc-1111-1111-1111-b779ab20e7dc/resourceGroups/RG258/providers/Microsoft.Compute/virtualMachines/VM1
VmId : e9d6b80b-1111-1111-1111-aeb5b1067a58
Name : VM1
Type : Microsoft.Compute/virtualMachines
Location : westus
Tags : {"environment":"production"}
HardwareProfile : {VmSize}
NetworkProfile : {NetworkInterfaces}
OSProfile : {ComputerName, AdminUsername, WindowsConfiguration, Secrets, AllowExtensionOperations, RequireGuestProvisionSignal}
ProvisioningState : Succeeded
StorageProfile : {ImageReference, OsDisk, DataDisks}
FullyQualifiedDomainName : vm1-b7af77.westus.cloudapp.azure.com
PS ###/clouddrive> New-AzKeyvault -name "Vault258new" -ResourceGroupName "RG258" -Location "westus" -EnabledForDiskEncryption
Vault Name : Vault258new
Resource Group Name : RG258
Location : westus
Resource ID : /subscriptions/35c3c9dc-1111-1111-1111-b779ab20e7dc/resourceGroups/RG258/providers/Microsoft.KeyVault/vaults/Vault258new
Vault URI : https://vault258new.vault.azure.net/
Tenant ID : fb52ca88-1111-1111-1111-99e632c3e070
SKU : Standard
Enabled For Deployment? : False
Enabled For Template Deployment? : False
Enabled For Disk Encryption? : True
Soft Delete Enabled? :
Access Policies :
Network Rule Set :
Default Action : Allow
Bypass : AzureServices
IP Rules :
Virtual Network Rules :
Tags :
Name Value
=========== ==========
environment production
WARNING: Access policy is not set. No user or application have access permission to use this vault. This can happen if the vault was created by a serviceprincipal. Please use Set-AzKeyVaultAccessPolicy to set access policies.
PS ###/clouddrive> Set-AzKeyVaultAccessPolicy -VaultName "Vault258new" -ResourceGroupName "RG258" -EnabledForDiskEncryption
Enable Azure Disk Encryption on volumes that are of all types
Before execute encryption scripts, the OS disk is not encrypted. This status could be retrieved from both the CLI and the portal.PS ###/clouddrive> Get-AzureRmVmDiskEncryptionStatus -ResourceGroupName "RG258" -VMName "VM1" tionKeyVaultId $KeyVaultResourceId -VolumeType "All"
OsVolumeEncrypted : Encrypted DataVolumesEncrypted : NotEncrypted OsVolumeEncryptionSettings : Microsoft.Azure.Management.Compute.Models.DiskEncryptionSettings ProgressMessage : Provisioning succeeded(On July 20, 2020:)
OsVolumeEncrypted : NotEncrypted DataVolumesEncrypted : NotEncrypted OsVolumeEncryptionSettings : ProgressMessage : No Encryption extension or metadata found on the VM
PS
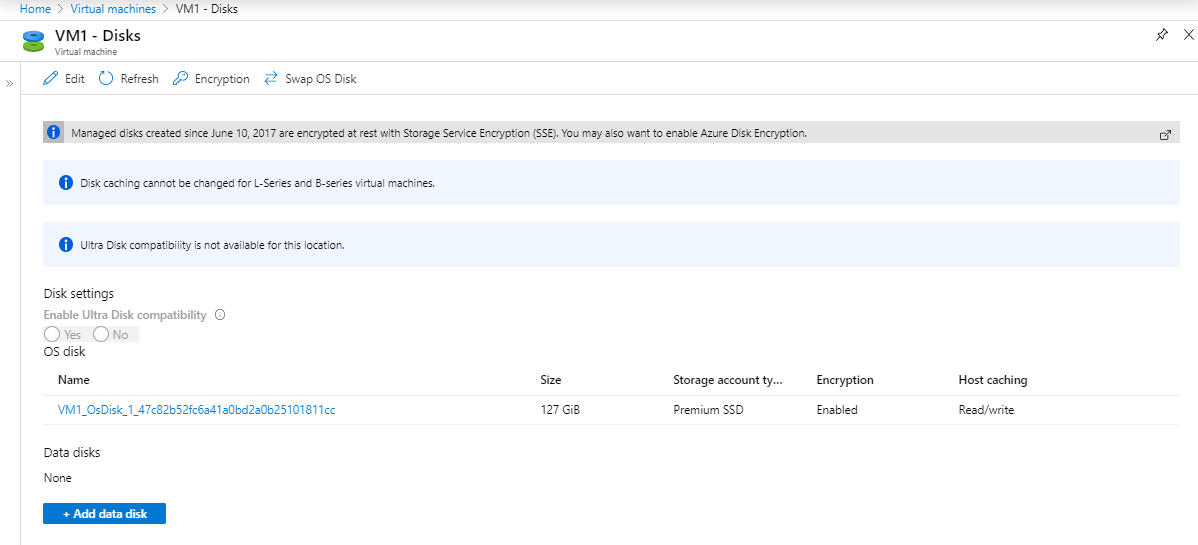
Show the status from the Azure portal.

Enable Azure Disk Encryption on volumes that are of all types. Execute the PowerShell script in CloudShell.
PS ###/clouddrive> vim ./create_vm1_ade.ps1
$KVRGname = "RG258" $VMRGName = 'RG258' $vmName = "VM1" $KeyVaultName = 'Vault258new' $KeyVault = Get-AzKeyVault -VaultName $KeyVaultName -ResourceGroupName $KVRGname $diskEncryptionKeyVaultUrl = $KeyVault.VaultUri $KeyVaultResourceId = $KeyVault.ResourceId Set-AzVMDiskEncryptionExtension -ResourceGroupName $VMRGname -VMName $vmName -DiskEncryptionKeyVaultUrl $diskEncryptionKeyVaultUrl -DiskEncryptionKeyVaultId $KeyVaultResourceId -VolumeType "All"
PS ###/clouddrive> ./create_vm1_ade.ps1
Enable AzureDiskEncryption on the VM
This cmdlet prepares the VM and enables encryption which may reboot the machine and takes 10-15 minutes to finish. Please save your work on the VM before confirming. Do you want to continue?
[Y] Yes [N] No [S] Suspend [?] Help (default is "Y"): Y
RequestId IsSuccessStatusCode StatusCode ReasonPhrase
--------- ------------------- ---------- ------------
True OK OK
After execute below command, check the encryption status of the OS disk.

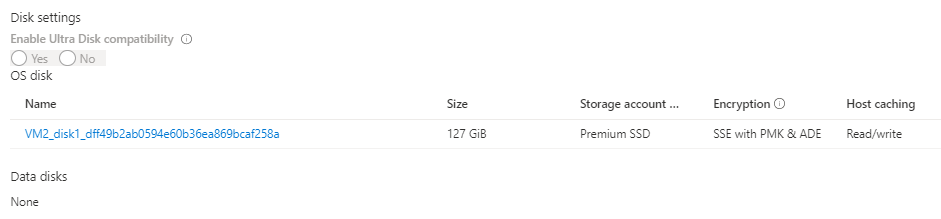
(On July 20, 2020:)

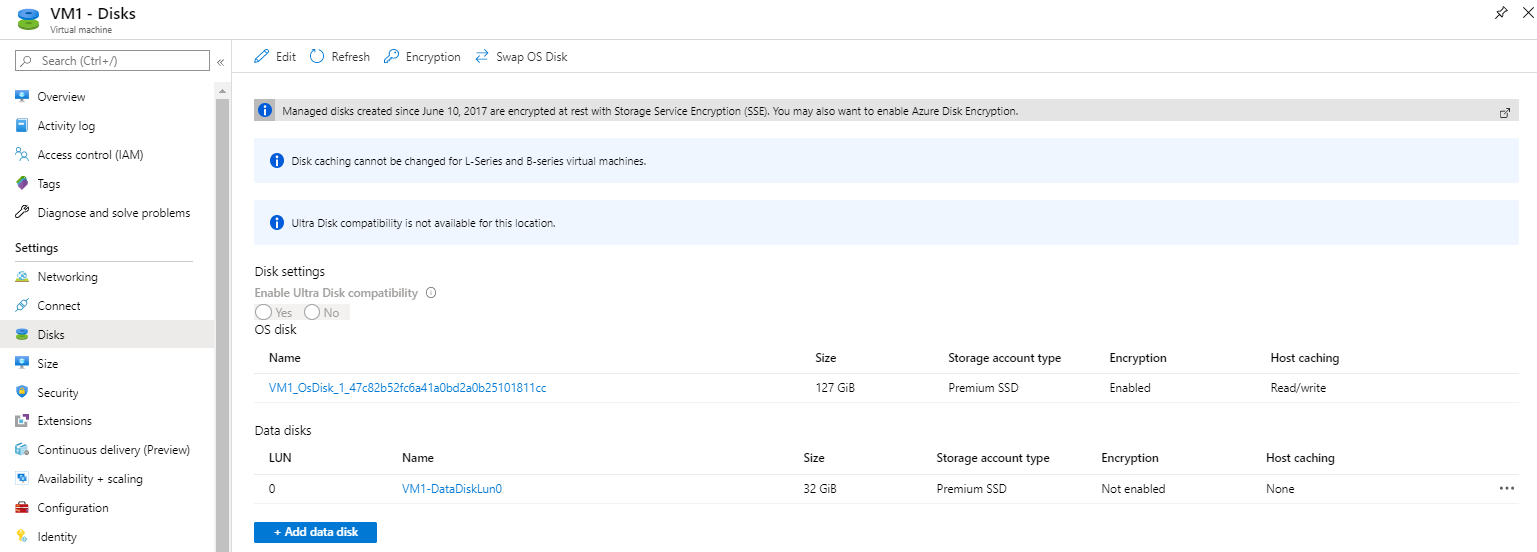
Create Data Disk
Create data disk.$diskConfig = New-AzDiskConfig ` -Location "WestUS" ` -CreateOption Empty ` -DiskSizeGB 32PS ###/clouddrive> $diskConfig = New-AzDiskConfig `
>> -Location "WestUS" `
>> -CreateOption Empty `
>> -DiskSizeGB 32
$dataDisk = New-AzDisk ` -ResourceGroupName "RG258" ` -DiskName "VM1-Disk3" ` -Disk $diskConfigPS ###/clouddrive> $dataDisk = New-AzDisk `
>> -ResourceGroupName "RG258" `
>> -DiskName "VM1-Disk3" `
>> -Disk $diskConfig
PS ###/clouddrive> $vm = Get-AzVM -ResourceGroupName "RG258" -Name "VM1"
PS ###/clouddrive> vim ./create_vm1_datadisk.ps1
$ResourceGroupName = "RG258" $VmName = "VM1" $DiskName = "VM1-DataDiskLun0" $diskConfig = New-AzDiskConfig -Location "WestUS" -CreateOption Empty -DiskSizeGB 32 -SkuName Premium_LRS $dataDisk = New-AzDisk -ResourceGroupName $ResourceGroupName -DiskName $DiskName -Disk $diskConfig $vm = Get-AzVM -ResourceGroupName $ResourceGroupName -Name $VmName $vm = Add-AzVMDataDisk -VM $vm -Name $DiskName -CreateOption Attach -ManagedDiskId $dataDisk.Id -Lun 0 Update-AzVM -ResourceGroupName $ResourceGroupName -VM $vmPS ###/clouddrive> ./create_vm1_datadisk.ps1
RequestId IsSuccessStatusCode StatusCode ReasonPhrase
--------- ------------------- ---------- ------------
True OK OK

Initialize Disk and create Partition
RDP to the Windows Server.Initialize Disk and create Partition, by executing below comamnd:
Get-Disk | Where partitionstyle -eq 'raw' |
Initialize-Disk -PartitionStyle MBR -PassThru |
New-Partition -AssignDriveLetter -UseMaximumSize |
Format-Volume -FileSystem NTFS -NewFileSystemLabel "myDataDisk" -Confirm:$false
PS C:\Users\scadmin> Get-Disk | Where partitionstyle -eq 'raw' |
>> Initialize-Disk -PartitionStyle MBR -PassThru |
>> New-Partition -AssignDriveLetter -UseMaximumSize |
>> Format-Volume -FileSystem NTFS -NewFileSystemLabel "myDataDisk" -Confirm:$false
DriveLetter FileSystemLabel FileSystem DriveType HealthStatus OperationalStatus SizeRemaining Size ----------- --------------- ---------- --------- ------------ ----------------- ------------- ---- I myDataDisk NTFS Fixed Healthy OK 31.92 GB 32 GB

PS C:\Users\scadmin> manage-bde -status F:
BitLocker Drive Encryption: Configuration Tool version 10.0.14393
Copyright (C) 2013 Microsoft Corporation. All rights reserved.
Volume F: [myDataDisk]
[Data Volume]
Size: 32.00 GB
BitLocker Version: None
Conversion Status: Fully Decrypted
Percentage Encrypted: 0.0%
Encryption Method: None
Protection Status: Protection Off
Lock Status: Unlocked
Identification Field: None
Automatic Unlock: Disabled
Key Protectors: None Found
Go to Azure CloudShell. Execute below command:
PS ###/clouddrive> vim create_vm1_ade_new_disk.ps1
$KVRGname = "RG258" $VMRGName = 'RG258' $vmName = "VM1" $KeyVaultName = 'Vault258new' $KeyVault = Get-AzKeyVault -VaultName $KeyVaultName -ResourceGroupName $KVRGname; $diskEncryptionKeyVaultUrl = $KeyVault.VaultUri; $KeyVaultResourceId = $KeyVault.ResourceId; $sequenceVersion = [Guid]::NewGuid(); Set-AzVMDiskEncryptionExtension -ResourceGroupName $VMRGname -VMName $vmName -DiskEncryptionKeyVaultUrl $diskEncryptionKeyVaultUrl -DiskEncryptionKeyVaultId $KeyVaultResourceId -VolumeType "All" –SequenceVersion $sequenceVersion;
PS ###/clouddrive> ./create_vm1_ade_new_disk.ps1
Enable AzureDiskEncryption on the VM
This cmdlet prepares the VM and enables encryption which may reboot the machine and takes 10-15 minutes to finish. Please save your work on the VM before confirming. Do you want to continue?
[Y] Yes [N] No [S] Suspend [?] Help (default is "Y"): Y
RequestId IsSuccessStatusCode StatusCode ReasonPhrase
--------- ------------------- ---------- ------------
True OK OK
PS C:\Users\scadmin> manage-bde -status F:
BitLocker Drive Encryption: Configuration Tool version 10.0.14393
Copyright (C) 2013 Microsoft Corporation. All rights reserved.
Volume F: [New Volume]
[Data Volume]
Size: 31.87 GB
BitLocker Version: 2.0
Conversion Status: Used Space Only Encrypted
Percentage Encrypted: 100.0%
Encryption Method: XTS-AES 256
Protection Status: Protection On
Lock Status: Unlocked
Identification Field: Unknown
Automatic Unlock: Enabled
Key Protectors:
External Key (Required for automatic unlock)
Numerical Password
PS ###/clouddrive> Get-AzureRmVmDiskEncryptionStatus -ResourceGroupName "RG258" -VMName "VM1"
OsVolumeEncrypted : Encrypted DataVolumesEncrypted : Encrypted OsVolumeEncryptionSettings : Microsoft.Azure.Management.Compute.Models.DiskEncryptionSettings ProgressMessage : [2.2.0.33]
References
Using the Resource Manager template
Get-AzureRmVMDiskEncryptionStatus
manage-bde -status c:
https://helpdesk.eoas.ubc.ca/kb/articles/how-to-check-status-of-bitlocker-encryption-on-a-client-on-windows-10
Appendix
Provision VMs with 8GB memory.Set-AzVMDiskEncryptionExtension: Long running operation failed with status 'Failed'. Additional Info:'VM has reported a failure when processing extension 'AzureDiskEncryptionForLinux'. Error message: "Not enough memory for enabling encryption on OS volume. 8 GB memory is recommended." More information on troubleshooting is available at https://aka.ms/vmextensionlinuxtroubleshoot ' ErrorCode: VMExtensionProvisioningError ErrorMessage: VM has reported a failure when processing extension 'AzureDiskEncryptionForLinux'. Error message: "Not enough memory for enabling encryptionon OS volume. 8 GB memory is recommended." More information on troubleshooting is available at https://aka.ms/vmextensionlinuxtroubleshoot ErrorTarget: StartTime: 2/23/2020 1:40:36 AM EndTime: 2/23/2020 1:41:05 AM OperationID: d79c2797-ab9a-4a93-8801-eb7905d06f9c Status: Failed
https://github.com/Azure/azure-quickstart-templates/tree/master/201-encrypt-running-windows-vm-without-aad
