Amazon GuardDuty EKS Runtime Monitoring
2024年02月14日
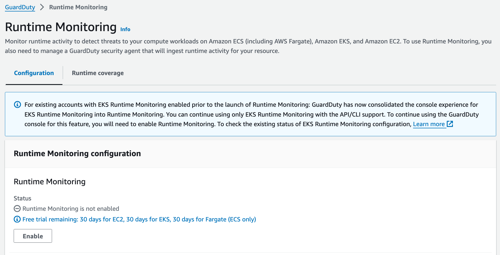
In the navigation pane, choose Runtime Monitoring.
Under the Configuration tab, choose Enable to enable Runtime Monitoring for your account.
For GuardDuty to receive the runtime events from an Amazon EKS cluster, I will manually manage GuardDuty agent (security agent?) for Amazon EKS cluster.
Look for an option related to "Integrations" or "Additional settings," where you might find EKS or Kubernetes-related settings.
Enable the feature for EKS cluster scanning or runtime monitoring. This might be labeled as "EKS Protection" or similar.
-
Use the following values for the parameters:
VPC_ID=<VPC-ID>
SUBNET_IDs=<subnet-IDs>
SG_IDs=<Security-Group-IDs>
Create IAM role.
Permissions: TBD
Trust policy:
EKS_cluster_name=<EKS_cluster_name>
Service_Account_Role_ARN=<service-account-role-ARN>
There are five t4g.medium EKS workloads running and being monitored for the entire month for runtime security threats in the Oregon Region, resulting in 10 vCPUs being monitored. GuardDuty continues to analyze and generate security findings based on VPC Flow Logs from EKS EC2 nodes in the account, resulting in 500 GB of VPC Flow Logs.
Total charges:
10 vCPUs * $1.50 per vCPU (for first 500 vCPUs)
+ 500 GB VPC Flow Logs (no charge for analysis of VPC Flow Logs from instances where the GuardDuty agent is deployed and active)
Total = $15 per month
Amazon GuardDuty Now Supports Amazon EKS Runtime Monitoring
Enabling GuardDuty Runtime Monitoring
Managing GuardDuty agent for Amazon EKS cluster manually
Prerequisites for Amazon EKS cluster support
create-vpc-endpoint
create-addon
DescribeAddonVersions
Amazon GuardDuty pricing
Prerequisites
Enable EKS Runtime Monitoring within Amazon GuardDuty and install the EKS add-on within your cluster, GuardDuty starts to consume runtime activity events from all EC2 hosts and containers in the cluster. These events are analyzed by GuardDuty for potential threats. As GuardDuty detects a potential threat, it generates a security finding. Navigate to the GuardDuty console to view the generated findings in your account.CPU and memory limits
The following table shows the CPU and memory limits for the Amazon EKS add-on for GuardDuty (aws-guardduty-agent).
| Parameter | Minimum limit | Maximum limit |
|---|---|---|
| CPU | 200m | 1000m |
| Memory | 256 Mi | 1024 Mi |
Enable GuardDuty (if not already enabled):
Navigate to the GuardDuty console in AWS. If GuardDuty is not already enabled, you will be prompted to enable it.In the navigation pane, choose Runtime Monitoring.
Under the Configuration tab, choose Enable to enable Runtime Monitoring for your account.
For GuardDuty to receive the runtime events from an Amazon EKS cluster, I will manually manage GuardDuty agent (security agent?) for Amazon EKS cluster.
Managing GuardDuty agent for Amazon EKS cluster manually
To manage agent manually, make sure to choose Disable in the Automated agent configuration section. Keep Runtime Monitoring enabled. To manage the security agent, see Managing GuardDuty agent for Amazon EKS cluster manually.
Enable Amazon EKS Cluster Scanning:
In the GuardDuty console, find the settings or configurations area.Look for an option related to "Integrations" or "Additional settings," where you might find EKS or Kubernetes-related settings.
Enable the feature for EKS cluster scanning or runtime monitoring. This might be labeled as "EKS Protection" or similar.
-
-
Select EKS Clusters for Monitoring:
- After enabling the feature, you may need to specify which EKS clusters GuardDuty should monitor. This can usually be done within the feature's settings.
- You might need to provide the ARN (Amazon Resource Name) of the EKS clusters you wish to monitor.
-
Configure Permissions:
- Ensure that GuardDuty has the necessary permissions to monitor your EKS clusters. This might involve updating IAM (Identity and Access Management) roles or policies to grant GuardDuty access to your EKS cluster data.
- You might need to create or update an IAM role that GuardDuty can assume to access EKS cluster logs and metrics.
-
Review and Adjust Settings:
- Review the configuration settings, such as log types to be monitored and notification settings.
- Adjust these settings based on your security and monitoring needs.
-
Monitor Findings:
- Once enabled, GuardDuty will start analyzing activities in your EKS clusters and generate findings for any detected anomalies or threats.
- Regularly check the GuardDuty console for findings and alerts related to your EKS clusters.
-
(Optional) Automate Response and Remediation:
- Consider setting up automation based on GuardDuty findings to quickly respond to and remediate detected threats. AWS Lambda functions can be used to automatically take actions based on specific types of findings.
Managing GuardDuty Agent for Amazon EKS Cluster Manually
Use the following values for the parameters:
- For Service name, enter
com.amazonaws.. Make sure to replaceus-east-1.guardduty-dataus-east-1with the correct Region. This must be the same Region as the EKS cluster that belongs to your AWS account ID. - For DNSOptions, enable private DNS option by setting it to
true.
VPC_ID=<VPC-ID>
SUBNET_IDs=<subnet-IDs>
SG_IDs=<Security-Group-IDs>
aws ec2 create-vpc-endpoint \
--vpc-id ${VPC_ID} \
--service-name com.amazonaws.us-west-2.guardduty-data \
--dns-options DnsRecordIpType=ipv4 \
--private-dns-enabled \
--vpc-endpoint-type Interface \
--subnet-ids ${SUBNET_IDs} \
--security-group-ids ${SG_IDs} \
--tag-specifications 'ResourceType=vpc-endpoint,Tags=[{Key=Name,Value=GuardDuty}]'
{
"VpcEndpoint": {
"VpcEndpointId": "vpce-03***c6",
"VpcEndpointType": "Interface",
"VpcId": "vpc-0b***30",
"ServiceName": "com.amazonaws.us-west-2.guardduty-data",
"State": "pending",
"RouteTableIds": [],
"SubnetIds": [
"subnet-00***91"
],
"Groups": [
{
"GroupId": "sg-03***93",
"GroupName": "guardduty-vpc-endpoint"
}
],
"IpAddressType": "ipv4",
"DnsOptions": {
"DnsRecordIpType": "ipv4"
},
"PrivateDnsEnabled": true,
"RequesterManaged": false,
"NetworkInterfaceIds": [
"eni-0b***8e"
],
"DnsEntries": [
{
"DnsName": "vpce-03***c6-6e***qi.guardduty-data.us-west-2.vpce.amazonaws.com",
"HostedZoneId": "Z1***9Z"
},
{
"DnsName": "vpce-03***c6-6e***qi-us-west-2a.guardduty-data.us-west-2.vpce.amazonaws.com",
"HostedZoneId": "Z1***9Z"
},
{
"DnsName": "guardduty-data.us-west-2.amazonaws.com",
"HostedZoneId": "ZONEIDPENDING"
}
],
"CreationTimestamp": "2024-02-14T04:57:35.045000+00:00",
"Tags": [
{
"Key": "Name",
"Value": "GuardDuty"
}
],
"OwnerId": "111122223333"
}
}
Create IAM role.
Permissions: TBD
Trust policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::124011853020:oidc-provider/oidc.eks.us-west-2.amazonaws.com/id/BFDB7DD511E66D7941F5A8DE12D8D49F"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"oidc.eks.us-west-2.amazonaws.com/id/BFDB7DD511E66D7941F5A8DE12D8D49F:aud": "sts.amazonaws.com",
"oidc.eks.us-west-2.amazonaws.com/id/BFDB7DD511E66D7941F5A8DE12D8D49F:sub": "system:serviceaccount:amazon-guardduty:aws-guardduty-agent"
}
}
}
]
}
EKS_cluster_name=<EKS_cluster_name>
Service_Account_Role_ARN=<service-account-role-ARN>
aws eks create-addon \
--cluster-name ${EKS_cluster_name} \
--addon-name aws-guardduty-agent \
--addon-version v1.4.1-eksbuild.2 \
--service-account-role-arn ${Service_Account_Role_ARN}
{
"addon": {
"addonName": "aws-guardduty-agent",
"clusterName": "example",
"status": "CREATING",
"addonVersion": "v1.4.1-eksbuild.2",
"health": {
"issues": []
},
"addonArn": "arn:aws:eks:us-west-2:<111122223333>:addon/<EKS-cluster-name>/aws-guardduty-agent/dac6d307-****-****-****-ef5a8907ff8d",
"createdAt": "2024-02-14T13:20:01.004000+08:00",
"modifiedAt": "2024-02-14T13:20:01.020000+08:00",
"serviceAccountRoleArn": "arn:aws:iam::<111122223333>:role/AmazonEKS_GuardDuty_EKS_Runtime_Monitoring_Role",
"tags": {}
}
}
Pricing Estimation
EKS Runtime Monitoring for EKS workloadsThere are five t4g.medium EKS workloads running and being monitored for the entire month for runtime security threats in the Oregon Region, resulting in 10 vCPUs being monitored. GuardDuty continues to analyze and generate security findings based on VPC Flow Logs from EKS EC2 nodes in the account, resulting in 500 GB of VPC Flow Logs.
Total charges:
10 vCPUs * $1.50 per vCPU (for first 500 vCPUs)
+ 500 GB VPC Flow Logs (no charge for analysis of VPC Flow Logs from instances where the GuardDuty agent is deployed and active)
Total = $15 per month
References
Amazon GuardDuty Now Supports Amazon EKS Runtime Monitoring
Enabling GuardDuty Runtime Monitoring
Managing GuardDuty agent for Amazon EKS cluster manually
Prerequisites for Amazon EKS cluster support
create-vpc-endpoint
create-addon
DescribeAddonVersions
Amazon GuardDuty pricing