Amazon EKS Security Group Setup
2024年02月14日
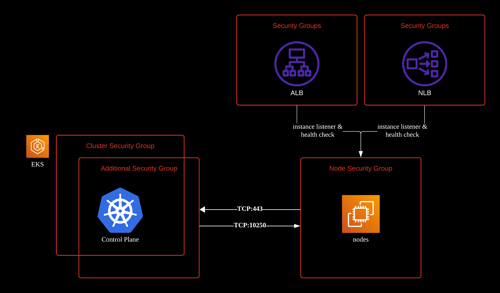
The cluster security group is a unified security group that is used to control communications between the Kubernetes control plane and compute resources on the cluster. The cluster security group is applied by default to the Kubernetes control plane managed by Amazon EKS as well as any managed compute resources created through the Amazon EKS API.
When you create a cluster, Amazon EKS creates a cluster security group that's named
The additional cluster security groups control communications from the Kubernetes control plane to compute resources.
This security group allows port 443 inbound from the worker node SG, so that the kubelets could communicate with the Kubernetes API server.
It also includes port 10250 for outbound traffic to the worker node SG; 10250 is the port that the kubelets listen on.
The worker node security groups are security groups applied to unmanaged worker nodes that control communications from worker nodes to the Kubernetes control plane.
The node group rules allow port 10250 inbound from the control plane SG and 443 outbound to the control plane SG.
To avoid port conflicts with sidecars, applications should not use any of the ports used by Envoy.
The following ports and protocols are used by the Istio control plane (istiod).
Amazon EKS security group requirements and considerations
Network security
Application Requirements
-
This topic describes the security group requirements of an Amazon EKS cluster.
Architecture

The cluster security group is a unified security group that is used to control communications between the Kubernetes control plane and compute resources on the cluster. The cluster security group is applied by default to the Kubernetes control plane managed by Amazon EKS as well as any managed compute resources created through the Amazon EKS API.
When you create a cluster, Amazon EKS creates a cluster security group that's named
eks-cluster-sg-<EKS-cluster-ID>. This security group has the following default rules:
| Rule type | Protocol | Ports | Source | Destination | Rule Category |
|---|---|---|---|---|---|
| Inbound | All | All | Self | N/A | Default rule |
| Outbound | All | All | N/A | 0.0.0.0/0 | Default rule |
The additional cluster security groups control communications from the Kubernetes control plane to compute resources.
This security group allows port 443 inbound from the worker node SG, so that the kubelets could communicate with the Kubernetes API server.
It also includes port 10250 for outbound traffic to the worker node SG; 10250 is the port that the kubelets listen on.
| Rule type | Protocol | Ports | Source | Destination | Rule Category |
|---|---|---|---|---|---|
| Inbound | TCP | 443 | Worker node SG | N/A | Minimum rule |
| Outbound | TCP | 10250 | N/A | Worker node SG | Minimum rule |
| Outbound | TCP | 8443 | N/A | Worker node SG | Knative web hook |
The worker node security groups are security groups applied to unmanaged worker nodes that control communications from worker nodes to the Kubernetes control plane.
The node group rules allow port 10250 inbound from the control plane SG and 443 outbound to the control plane SG.
| Rule type | Protocol | Ports | Source | Destination | Rule Category |
|---|---|---|---|---|---|
| Inbound | ICMP (for IPv4) - Destination Unreachable | fragmentation required, and DF flag set | Self | N/A | Recommended rule |
| Inbound | TCP | Instance listener | ALB SG | N/A | ALB and TG required rule |
| Inbound | TCP | Health check | ALB SG | N/A | ALB and TG required rule |
| Inbound | TCP | Instance listener and health check | NLB SG | N/A | NLB and TG required rule |
| Inbound | All | All | Self | N/A | Minimum rule |
| Inbound | TCP | 10250 | Additional cluster SG | N/A | Minimum rule |
| Inbound | TCP | 443 | Additional cluster SG | N/A | Known requirements: - Istio (refer to below "Ports used by Istio" section) |
| Inbound | TCP | 8443 | Additional cluster SG | N/A | Knative web hook |
| Outbound | All | All | N/A | 0.0.0.0/0 | Default rule |
Ports used by Istio
The following ports and protocols are used by the Istio sidecar proxy (Envoy).To avoid port conflicts with sidecars, applications should not use any of the ports used by Envoy.
| Port | Protocol | Description | Pod-internal only | Status |
|---|---|---|---|---|
| 15000 | TCP | Envoy admin port (commands/diagnostics) | Yes | |
| 15001 | TCP | Envoy outbound | No | |
| 15004 | HTTP | Debug port | Yes | |
| 15006 | TCP | Envoy inbound | No | |
| 15008 | H2 | HBONE mTLS tunnel port | No | |
| 15009 | H2C | HBONE port for secure networks | No | |
| 15020 | HTTP | Merged Prometheus telemetry from Istio agent, Envoy, and application | No | |
| 15021 | HTTP | Health checks | No | |
| 15053 | DNS | DNS port, if capture is enabled | Yes | |
| 15090 | HTTP | Envoy Prometheus telemetry | No |
The following ports and protocols are used by the Istio control plane (istiod).
| Port | Protocol | Description | Local host only | Status |
|---|---|---|---|---|
| 443 | HTTPS | Webhooks service port | No | Applied |
| 8080 | HTTP | Debug interface (deprecated, container port only) | No | N/A |
| 15010 | GRPC | XDS and CA services (Plaintext, only for secure networks) | No | |
| 15012 | GRPC | XDS and CA services (TLS and mTLS, recommended for production use) | No | |
| 15014 | HTTP | Control plane monitoring | No | |
| 15017 | HTTPS | Webhook container port, forwarded from 443 | No | Applied |
References
Amazon EKS security group requirements and considerations
Network security
Application Requirements
-