Cross AWS Account to Manage EKS Cluster Using kubectl
2024年06月15日
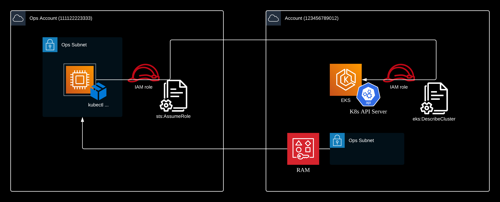
Account A:
Account ID: 123456789012
IAM role: roleA
Account B:
Account ID: 111122223333
IAM role: roleB
IAM role A on the same AWS account as the EKS cluster:
This IAM role has been attached with the following policy:
Role B
Role B is actually the instance profile that associated to the EC2 instance, which is used to remotely execute management commands to the container stack, e.g., kubectl, istioctl and etc.
Besides other necessary IAM permissions, this IAM role has been attached with the following policy:
The EC2 instance spec:
t4g.nano
The commands executed in the article is from a ARM CPU-architecture environment.
1. Download the latest release with the command:
$ curl -LO "https://dl.k8s.io/release/$(curl -L -s https://dl.k8s.io/release/stable.txt)/bin/linux/arm64/kubectl"
2. Install kubectl
$ sudo install -o root -g root -m 0755 kubectl /usr/local/bin/kubectl
3.
$ kubectl version --client
# ISTIO_VER=1.23.2
# curl -kL https://istio.io/downloadIstioctl | ISTIO_VERSION=${ISTIO_VER} TARGET_ARCH=$(uname -m) sh -
2. Add the
$ sudo cp $HOME/.istioctl/bin/istioctl /usr/local/bin/
$ istioctl version
If error message "error: You must be logged in to the server (Unauthorized)" is received while using kubectl commands to connect to the Amazon EKS API server, refer to How to Handle Error: "You must be logged in to the server (Unauthorized)".
On the container stack management server, configure the config file to obtain the credentials from the hosting Amazon EC2 instance metadata.
# mkdir -p .aws
Content of the config file
# aws eks update-kubeconfig --region <Region> --name <eks-cluster-name>
Output:
Configuration and credential file settings
In order for kubectl to find and access a Kubernetes cluster, it needs a kubeconfig file. By default, kubectl configuration is located at ~/.kube/config.
Get the latest version of aws-iam-authenticator
Get the latest version of aws-iam-authenticator from https://us-west-2.console.aws.amazon.com/s3/buckets/amazon-eks?region=us-west-2&bucketType=general&tab=objects
Architecture

Account A:
Account ID: 123456789012
IAM role: roleA
Account B:
Account ID: 111122223333
IAM role: roleB
IAM role A on the same AWS account as the EKS cluster:
This IAM role has been attached with the following policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"eks:DescribeCluster"
"eks:UpdateClusterVersion",
"eks:DescribeUpdate"
],
"Resource": "arn:aws:eks:<region>:111122223333:cluster/<eks-cluster-name>"
}
]
}
Trust relationships:{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789012:role/roleB"
},
"Action": "sts:AssumeRole",
"Condition": {}
}
]
}
Role B
Role B is actually the instance profile that associated to the EC2 instance, which is used to remotely execute management commands to the container stack, e.g., kubectl, istioctl and etc.
Besides other necessary IAM permissions, this IAM role has been attached with the following policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"sts:AssumeRole"
],
"Resource": "arn:aws:iam::111122223333:role/roleA"
},
{
"Effect": "Allow",
"Action": [
"eks:DescribeCluster"
],
"Resource": "arn:aws:eks:<region>:111122223333:cluster/<eks-cluster-name>"
}
]
}
The EC2 instance spec:
t4g.nano
The commands executed in the article is from a ARM CPU-architecture environment.
Prerequisites
Install kubectl
Install kubectl binary with curl on Linux1. Download the latest release with the command:
$ curl -LO "https://dl.k8s.io/release/$(curl -L -s https://dl.k8s.io/release/stable.txt)/bin/linux/arm64/kubectl"
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 138 100 138 0 0 1235 0 --:--:-- --:--:-- --:--:-- 1243
100 47.6M 100 47.6M 0 0 122M 0 --:--:-- --:--:-- --:--:-- 122M
2. Install kubectl
$ sudo install -o root -g root -m 0755 kubectl /usr/local/bin/kubectl
3.
$ kubectl version --client
Client Version: v1.30.2 Kustomize Version: v5.0.4-0.20230601165947-6ce0bf390ce3
Install Istioctl
Install theistioctl binary with curl
1. Download the latest release# ISTIO_VER=1.23.2
# curl -kL https://istio.io/downloadIstioctl | ISTIO_VERSION=${ISTIO_VER} TARGET_ARCH=$(uname -m) sh -
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 96 100 96 0 0 1532 0 --:--:-- --:--:-- --:--:-- 1523
100 4636 100 4636 0 0 21722 0 --:--:-- --:--:-- --:--:-- 21722
Downloading istioctl-1.21.3 from https://github.com/istio/istio/releases/download/1.21.3/istioctl-1.21.3-linux-arm64.tar.gz ...
istioctl-1.21.3-linux-arm64.tar.gz download complete!
Add the istioctl to your path with:
export PATH=$HOME/.istioctl/bin:$PATH
Begin the Istio pre-installation check by running:
istioctl x precheck
Need more information? Visit https://istio.io/docs/reference/commands/istioctl/
2. Add the
istioctl client to the path that could be executed from command line.$ sudo cp $HOME/.istioctl/bin/istioctl /usr/local/bin/
$ istioctl version
client version: 1.23.2 control plane version: 1.22.1 data plane version: 1.22.1 (13 proxies)
If error message "error: You must be logged in to the server (Unauthorized)" is received while using kubectl commands to connect to the Amazon EKS API server, refer to How to Handle Error: "You must be logged in to the server (Unauthorized)".
On the container stack management server, configure the config file to obtain the credentials from the hosting Amazon EC2 instance metadata.
# mkdir -p .aws
Content of the config file
.aws/config:[default] role_arn=arn:aws:iam::111122223333:role/roleA credential_source=Ec2InstanceMetadata region = <region>
# aws eks update-kubeconfig --region <Region> --name <eks-cluster-name>
Output:
Added new context arn:aws:eks:<region>:111122223333:cluster/<eks-cluster-name> to /root/.kube/config
References
Configuration and credential file settings
Archived
Verify kubectl configurationIn order for kubectl to find and access a Kubernetes cluster, it needs a kubeconfig file. By default, kubectl configuration is located at ~/.kube/config.
Get the latest version of aws-iam-authenticator
Get the latest version of aws-iam-authenticator from https://us-west-2.console.aws.amazon.com/s3/buckets/amazon-eks?region=us-west-2&bucketType=general&tab=objects