Integrate AWS NLB with Istio Service Mesh
2021年04月08日
ISTIO_VERSION=1.8.4
curl -L https://istio.io/downloadIstio | sh -
Move to the Istio package directory.
cd istio-1.8.4
This directory contains contents under below sub-directories as well as other sub-directories for other use:
Add the istioctl client to the variable PATH.
export PATH=$PWD/bin:$PATH
Add below line in file istio-{RELEASE_TAG}/manifests/charts/gateways/istio-ingress/values.yaml, to create an internal NLB (network load balancer) using istioctl.
To use AWS NLB, it is necessary to add an AWS specific annotation to the Istio installation.
In addition, to meet security requirements so as not to expose directly to the Internet, I use the internal NLB, instead of the Internet-facing one.
$ vim manifests/charts/gateways/istio-ingress/values.yaml
Setup Istio ingress gateway within EKS cluster.
$ istioctl install --set profile=demo --charts=./manifests/ \
> --set components.cni.enabled=true \
> --set components.cni.namespace=kube-system
Verify that there is a new load balancer has been provisioned.
$ aws elbv2 describe-load-balancers | grep LoadBalancerName
$ aws elbv2 describe-load-balancers --names a32a****d079
Deploy a Knative Serving application, and make it accessible by the main application.
Configure DNS resolution using Route 53.
$ vim setup-dns-record.json
$ aws route53 change-resource-record-sets --hosted-zone-id ZL***5O --change-batch file://setup-dns-record.json
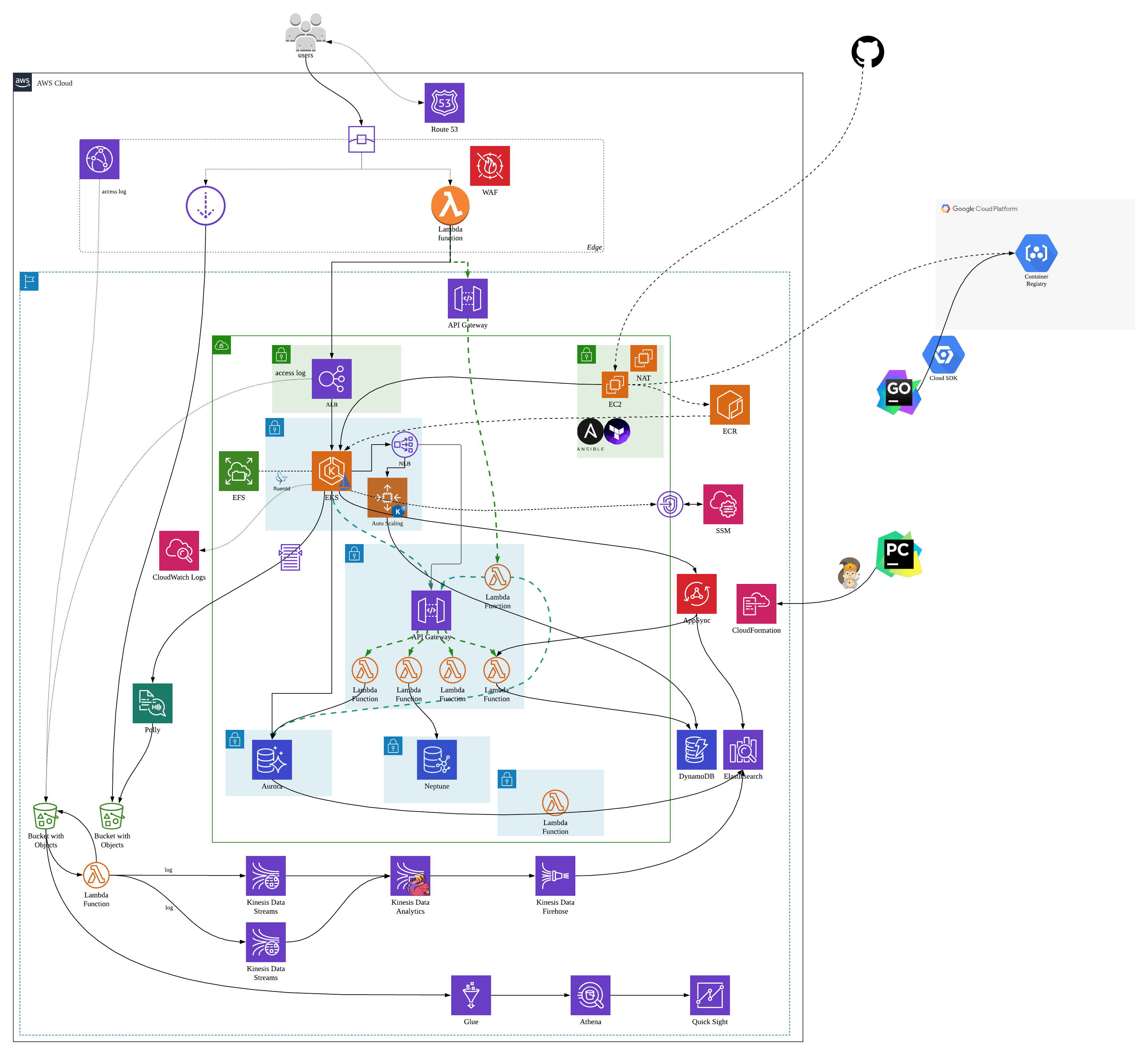
After refactoring the architecture, the full picture of the application architecture has become:
References
Istio Ingress Gateway using Network load balancer on EKS
Proxy protocol on AWS NLB and Istio ingress gateway
-
By default, when we provision Istio in AWS, it will automatically provision a classic load balancer, which is the previous generation and hence is not what we want.
We will have a main application running inside a EKS worker node. It will make API calls towards a micro service via NLB.
$ aws elbv2 describe-load-balancers | grep LoadBalancerName
"LoadBalancerName": "c0**43-blog-blogingress-6**4",Download and extract Istio version 1.8.4. I chose this version to be compatible with Knative, which is another topic.
ISTIO_VERSION=1.8.4
curl -L https://istio.io/downloadIstio | sh -
Move to the Istio package directory.
cd istio-1.8.4
This directory contains contents under below sub-directories as well as other sub-directories for other use:
- Sample applications in samples/
- The istioctl client binary in the bin/ directory.
Add the istioctl client to the variable PATH.
export PATH=$PWD/bin:$PATH
Add below line in file istio-{RELEASE_TAG}/manifests/charts/gateways/istio-ingress/values.yaml, to create an internal NLB (network load balancer) using istioctl.
To use AWS NLB, it is necessary to add an AWS specific annotation to the Istio installation.
In addition, to meet security requirements so as not to expose directly to the Internet, I use the internal NLB, instead of the Internet-facing one.
$ vim manifests/charts/gateways/istio-ingress/values.yaml
...
serviceAnnotations:
service.beta.kubernetes.io/aws-load-balancer-type: "nlb"
service.beta.kubernetes.io/aws-load-balancer-internal: "true"
...
Setup Istio ingress gateway within EKS cluster.
$ istioctl install --set profile=demo --charts=./manifests/ \
> --set components.cni.enabled=true \
> --set components.cni.namespace=kube-system
This will install the Istio demo profile with ["Istio core" "Istiod" "CNI" "Ingress gateways" "Egress gateways"] components into the cluster. Proceed? (y/N) y ✔ Istio core installed ✔ Istiod installed ✔ CNI installed ✔ Egress gateways installed ✔ Ingress gateways installed ✔ Installation complete
Verify that there is a new load balancer has been provisioned.
$ aws elbv2 describe-load-balancers | grep LoadBalancerName
"LoadBalancerName": "a32a****d079",
"LoadBalancerName": "c0**43-blog-blogingress-6**4",
Check the AWS console — EC2/Load Balancers section to see if the NLB has been provisioned with scheme internal.$ aws elbv2 describe-load-balancers --names a32a****d079
{
"LoadBalancers": [
{
"IpAddressType": "ipv4",
"VpcId": "vpc-0b***30",
"LoadBalancerArn": "arn:aws:elasticloadbalancing:us-west-2:123456789012:loadbalancer/net/a3***79/70***9d",
"State": {
"Code": "active"
},
"DNSName": "a3***79-70***9d.elb.us-west-2.amazonaws.com",
"LoadBalancerName": "a3***79",
"CreatedTime": "2021-04-09T09:24:37.438Z",
"Scheme": "internal",
"Type": "network",
"CanonicalHostedZoneId": "Z1***5G",
"AvailabilityZones": [
{
"SubnetId": "subnet-0c***3d",
"LoadBalancerAddresses": [],
"ZoneName": "us-west-2b"
},
{
"SubnetId": "subnet-01***50",
"LoadBalancerAddresses": [],
"ZoneName": "us-west-2a"
}
]
}
]
}
Deploy a Knative Serving application, and make it accessible by the main application.
Configure DNS resolution using Route 53.
$ vim setup-dns-record.json
{
"Changes": [
{
"Action": "CREATE",
"ResourceRecordSet": {
"Name": "*.default.tianzhui.cloud",
"Type": "CNAME",
"TTL": 60,
"ResourceRecords": [{ "Value": "a3***79-70***9d.elb.us-west-2.amazonaws.com"}]
}
}
]
}
$ aws route53 change-resource-record-sets --hosted-zone-id ZL***5O --change-batch file://setup-dns-record.json
{
"ChangeInfo": {
"Status": "PENDING",
"SubmittedAt": "2021-04-09T15:15:54.548Z",
"Id": "/change/C08452052VWPDG65SYTG5"
}
}
After refactoring the architecture, the full picture of the application architecture has become:

References
Istio Ingress Gateway using Network load balancer on EKS
Proxy protocol on AWS NLB and Istio ingress gateway
-