Use custom domain and in-transit encryption for applications hosted by AWS Fargate
In the previous blog post, implement enterprise application with custom name and private traffic, I have demonstrate how to deploy EKS-based application into a private network environment, with custom domain name allocated for the application to be accessed.
Begin with this post, I will use a series of posts to illustrate how to implement a similar setup with AWS ECS Fargate, to encrypt the traffic in-transit, and keep the traffic stay within the VPC environment.
To do that, I mainly leveraged below services and primitive solutions to achieve the requirements.
- VPC
- Route 53
- API Gateway
- NLB and ALB
- ACM
- Fargate
There will be detail explanation of how these services are utilized. The above list is only an overall depiction.
The following is the architecture diagram. The EC2 instance in the diagram is nothing but a test machine.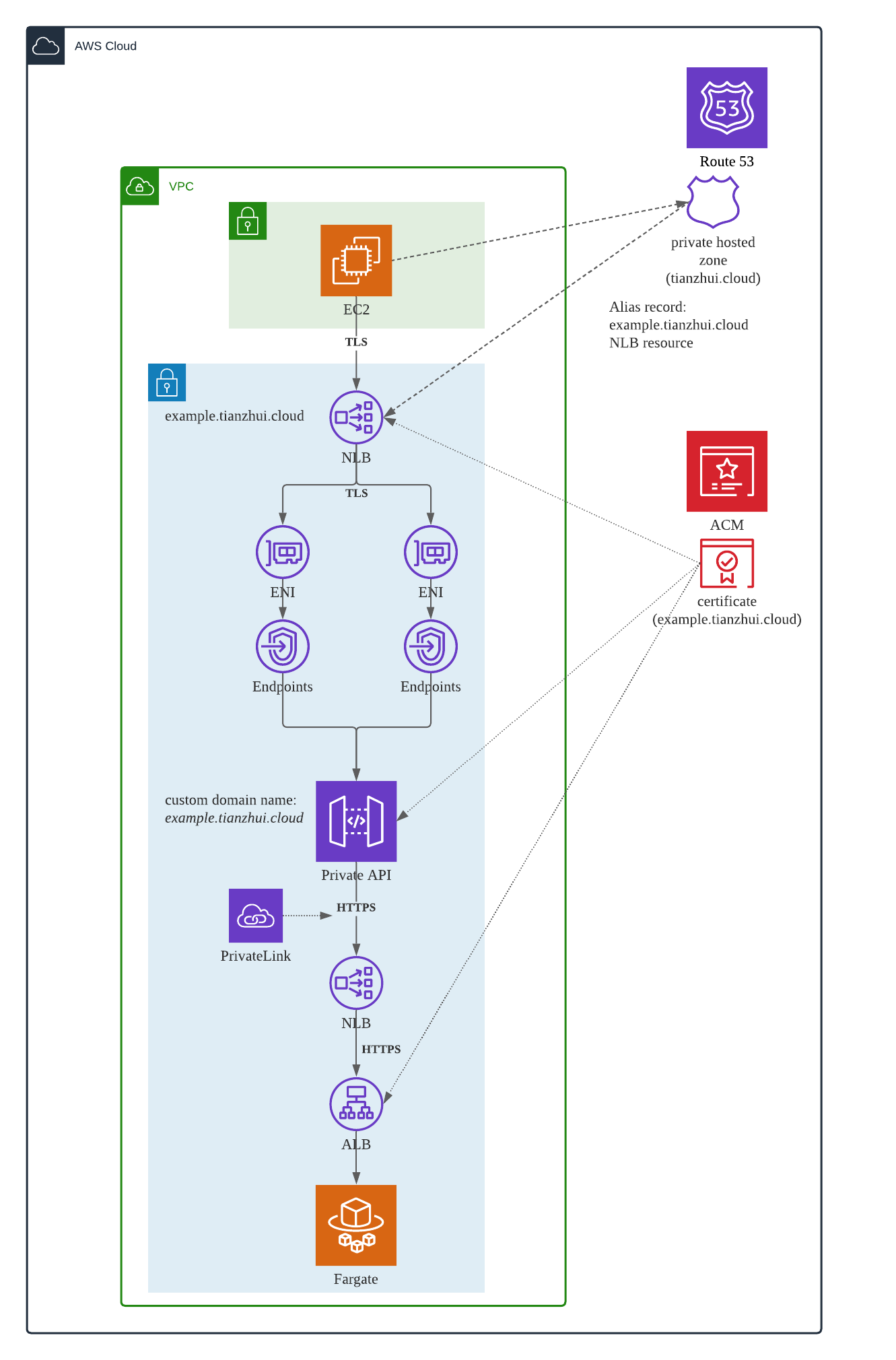
Network Considerations
To guarantee that all network traffic stays within the VPC environment, below components have been selected.
- Internal NLB
- Internal ALB
- Route 53 private host zone
- Fargate - the ECS cluster service does not have public IP assigned
- Private API fronted by VPC endpoint
- VPC link for API Gateway supported by private link
- Security groups that only allow expected IP ranges, ports etc.
In addition, to make sure the private API could only be accessed within VPC, a resource policy has been implemented to control the access.
Security Considerations
To ensure the network traffic are encrypted, below components and features have been selected and implemented.
- ACM
- NLB with TLS listener. Choose the communication protocol TLS to be used between NLB and its targets, so that communication is encrypted. This helps encrypt traffic in-transit between NLB and API gateway.
- ALB with HTTPS listener
- API Gateway with certificate
- Security groups only allow protocol TCP and port 443
Non-technical Considerations
To let users and components use custom domain name, below components and features have been selected and implemented.
- Route 53 private host zone
- API gateway custom domain name
- API private integration - URI point to the custom domain name (https://example.tianzhui.cloud)
- Fronted NLB and backend ALB - associated with ACM certificate
- Disabling the default endpoint for a REST API. By default, clients can invoke your API by using the execute-api endpoint that API Gateway generates for your API. To ensure that clients can access your API only by using a custom domain name, disable the default execute-api endpoint. After you disable the default endpoint, you must deploy your API for the change to take effect.
References
New – TLS Termination for Network Load Balancers
Understanding VPC links in Amazon API Gateway private integrations
Disabling the default endpoint for a REST API
-